What is a next-generation firewall (NGFW)?
A next-generation firewall (NGFW) has additional capabilities that separate it from a traditional firewall. NGFWs are often better at identifying the latest threats.
Learning Objectives
After reading this article you will be able to:
- Define next-generation firewall (NGFW)
- Describe NGFW capabilities
- Differentiate between packet filtering and deep packet inspection (DPI)
Related Content
Want to keep learning?
Subscribe to theNET, Cloudflare's monthly recap of the Internet's most popular insights!
Copy article link
What is a next-generation firewall (NGFW)?
A next-generation firewall (NGFW) is a security appliance that processes network traffic and applies rules to block potentially dangerous traffic. NGFWs evolve and expand upon the capabilities of traditional firewalls. They do all that firewalls do, but more powerfully and with additional features.
Consider two airport security agencies. One checks to make sure passengers are not on any no-fly lists, that their identities match what is listed on their tickets, and that they are going to destinations the airport actually serves. The second one, in addition to checking no-fly lists and so on, inspects what the passengers are carrying, making sure they do not have dangerous or disallowed items. The first agency keeps airports secure from obvious threats; the second also identifies threats that may be less obvious.
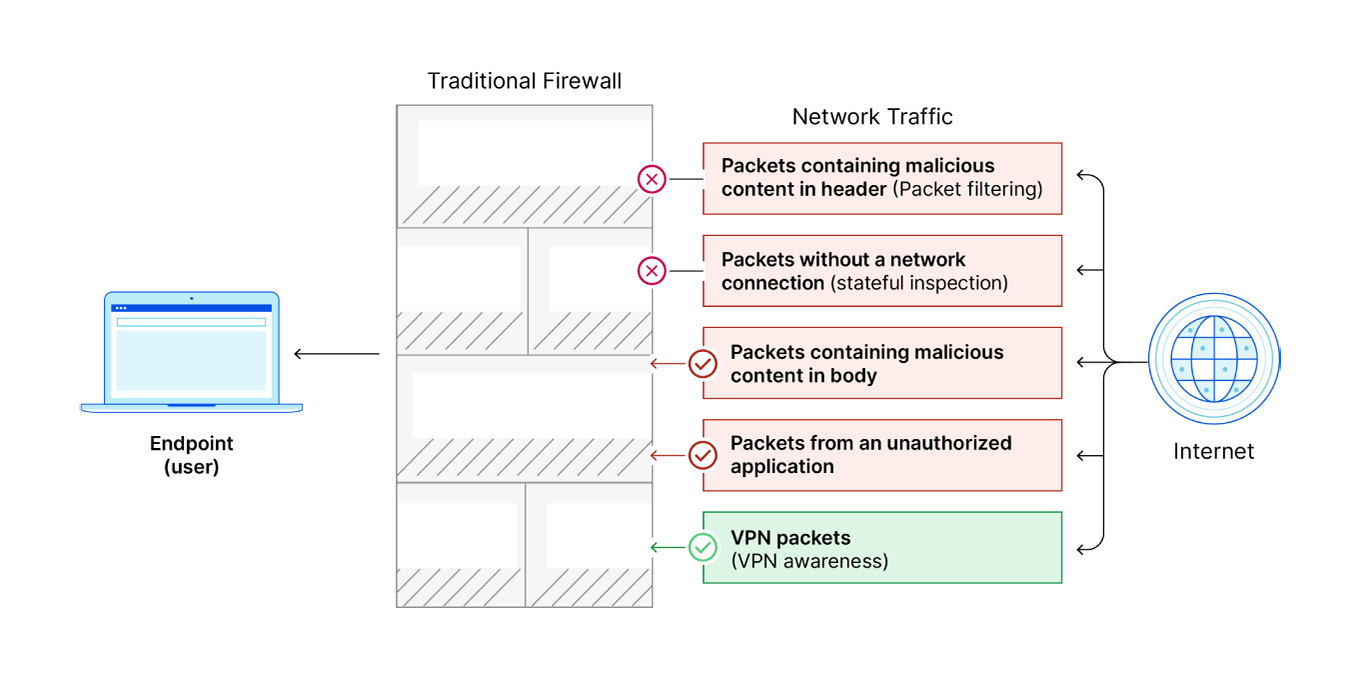
An ordinary firewall is like the first security agency: it blocks or allows data (passengers) based on where it is going, whether or not it is part of a legitimate network connection, and where it comes from. An NGFW is more like the second security agency: it inspects data on a deeper level to identify and block threats that may be hidden in normal-seeming traffic.
What capabilities does an NGFW have?
NGFWs can do everything that regular firewalls can do. This includes:
- Packet filtering: Inspecting each individual packet of data and blocking dangerous or unexpected packets. Packet filtering is explained more below.
- Stateful inspection: Looking at packets in context to make sure they are part of a legitimate network connection.
- VPN awareness: Firewalls are able to identify encrypted VPN traffic and allow it through.
NGFWs also add several capabilities that older firewalls do not have. NGFWs use deep packet inspection (DPI) in addition to packet filtering. And according to Gartner, a global research and advisory firm, an NGFW includes:
- Application awareness and control
- Intrusion prevention
- Threat intelligence
- Paths for upgrading in order to add future information feeds
- Techniques to address evolving security threats
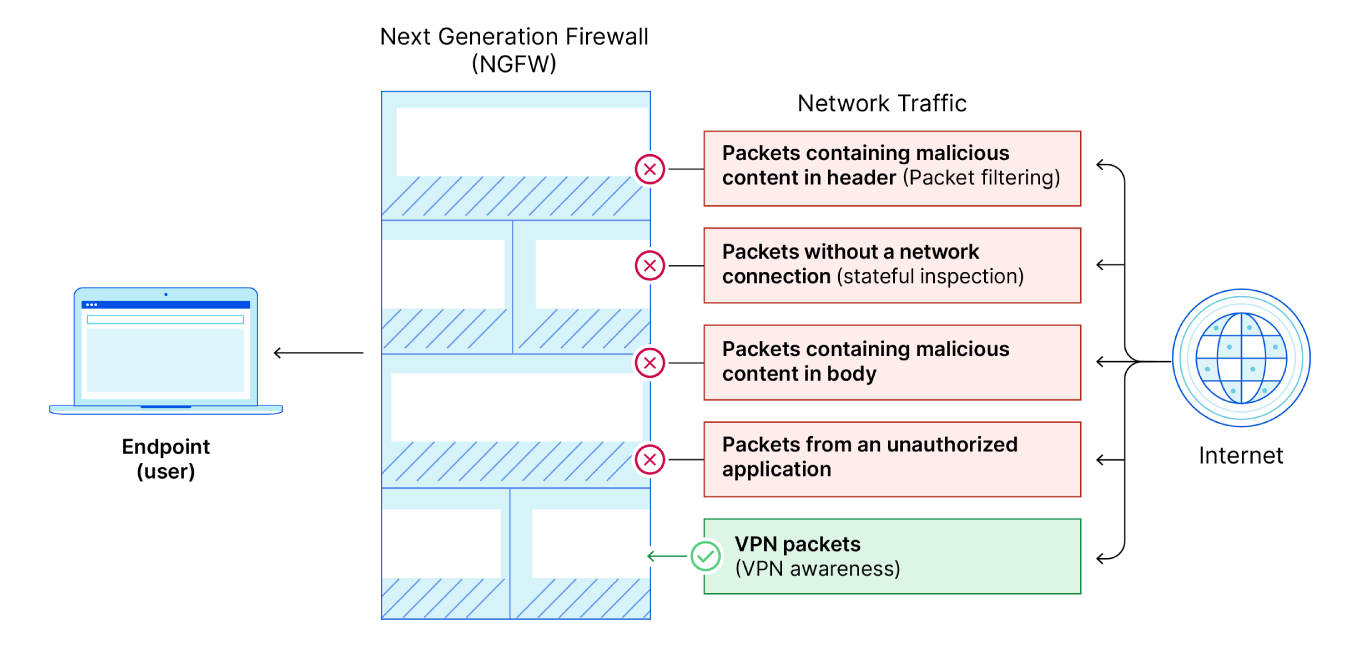
These capabilities are explained in detail below.
Most of these features are possible because, unlike regular firewalls, NGFWs can process traffic at several layers in the OSI model, not just layers 3 (the network layer) and 4 (the transport layer). NGFWs can look at layer 7 HTTP traffic and identify which applications are in use, for instance. This is an important capability because layer 7 (the application layer) is increasingly used for attacks to get around the security policies applied at layers 3 and 4 by traditional firewalls.
(To learn more about the OSI layers, see What is the OSI model?)
What are packet filtering and deep packet inspection (DPI)?
Packet filtering
All data that traverses a network or the Internet is broken down into smaller pieces called packets. Because these packets contain the content that enters a network, firewalls inspect them and block or allow them to prevent malicious content (such as a malware attack) from getting through. All firewalls have this packet filtering capability.
Packet filtering works by inspecting the source and destination IP addresses, ports, and protocols associated with each packet — in other words, where each packet comes from, where it is going, and how it will get there. Firewalls allow or block packets based on this assessment, filtering out the disallowed packets.
As an example, attackers sometimes try to exploit vulnerabilities associated with the Remote Desktop Protocol (RDP) by sending specially crafted packets to the port used by this protocol, port 3389. However, a firewall can inspect a packet, see which port it is going to, and block all packets directed at that port — unless they are from a specifically allowed IP address. This involves inspecting network traffic at layers 3 (to see source and destination IP addresses) and 4 (to see the port).
Deep packet inspection (DPI)
NGFWs improve upon packet filtering by instead performing deep packet inspection (DPI). Like packet filtering, DPI involves inspecting every individual packet to see source and destination IP address, source and destination port, and so on. This information is all contained in the layer 3 and layer 4 headers of a packet.
But DPI also inspects the body of each packet, not just the header. Specifically, DPI checks packet bodies for malware signatures and other potential threats. It compares the contents of each packet to the contents of known malicious attacks.
What is application awareness and control?
NGFWs block or allow packets based on which application they are going to. They do so by analyzing traffic at layer 7, the application layer. Traditional firewalls do not have this capability because they only analyze traffic at layers 3 and 4.
Application awareness allows administrators to block potentially risky applications. If an application's data cannot get past the firewall, then it cannot introduce threats into the network.
According to Gartner's definitions of the terms, both this capability and intrusion prevention (described below) are elements of DPI.
What is intrusion prevention?
Intrusion prevention analyzes incoming traffic, identifies known threats and potential threats, and blocks those threats. Such a feature is often called an intrusion prevention system (IPS). NGFWs include IPSes as part of their DPI capabilities.
IPSes can use several methods to detect threats, including:
- Signature detection: Scanning the information within incoming packets and comparing it to known threats
- Statistical anomaly detection: Scanning traffic to detect unusual changes in behavior, as compared to a baseline
- Stateful protocol analysis detection: Similar to statistical anomaly detection, but focused on the network protocols in use and comparing them to typical protocol usage
What is threat intelligence?
Threat intelligence is information about potential attacks. Because attack techniques and malware strains are continually changing, up-to-date threat intelligence is crucial for blocking those attacks. NGFWs are able to receive and act on threat intelligence feeds from external sources.
Threat intelligence keeps IPS signature detection effective by providing the latest malware signatures.
Threat intelligence can also supply IP reputation information. "IP reputation" identifies IP addresses where attacks (especially bot attacks) often come from. A feed of IP reputation threat intelligence provides the latest known bad IP addresses, which an NGFW can then block.
Are next-gen firewalls hardware-based or software-based?
Some NGFWs are hardware appliances designed to defend an internal private network. NGFWs can also be deployed as software, but they do not need to be software-based to be considered next-generation.
Finally, an NGFW can be deployed as a cloud service; this is called a cloud firewall or firewall-as-a-service (FWaaS). FWaaS is an important component of secure access service edge (SASE) networking models. (Compare NGFW and FWaaS in more depth.)
What is Cloudflare Magic Firewall?
Cloudflare Magic Firewall is a network-level firewall delivered through the global Cloudflare network. It protects users, office networks, and cloud infrastructure, and it is designed to replace hardware-based firewalls with advanced, scalable protection.
Magic Firewall is tightly integrated with Cloudflare One, a SASE platform that combines networking and security services.